Memory Investigation
Category: Reverse - Points: 100 - Solves: Description: It's all about execution. The flag is of the form HACKDAY{return}
Solution:
To solve this challenge you need to find the return value.
So to find the flag, we need to understand how the program work.
To test him we put the command ./challenge1.elf then ./challenge1.elf FLAG. The results are here :
 Without key we received the "Segmentation Fault" message but with a key we have a good message.
So to decompile and see the program code, we need to use Ghidra and find the good function who generate the flag (return).
To find them, we use the "Search > For Strings... > Search" and write "LUCK" in the input to find the place :
Without key we received the "Segmentation Fault" message but with a key we have a good message.
So to decompile and see the program code, we need to use Ghidra and find the good function who generate the flag (return).
To find them, we use the "Search > For Strings... > Search" and write "LUCK" in the input to find the place :

 With the decompile code (right part), we can see that's the func2 function who generate the flag.
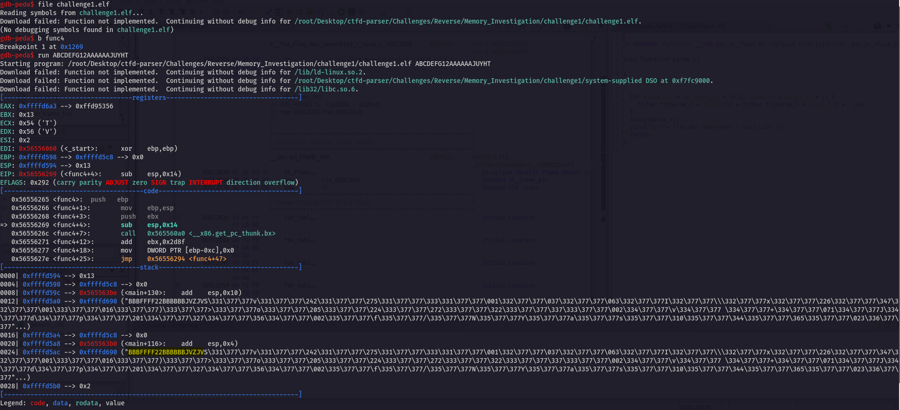
So now we want to run the program with gdb-peda to break at the func2 and see the return value :
With the decompile code (right part), we can see that's the func2 function who generate the flag.
So now we want to run the program with gdb-peda to break at the func2 and see the return value :
Last updated