En construction !
Category: Web - Points: 999 - Difficulty : Moyen - Solves : 36
Description: Nous avons trouvé un nouveau site web mis en place par Hallebarde, mais il ne semble pas y avoir grand-chose dessus. Cependant la forte quantité de trafic détectée laisse à penser que Hallebarde l'utiliserait pour faire passer des messages secrets. Pourriez-vous jeter un oeil ?
Aucun outil de automatisé de bruteforce n'est nécessaire pour ce challenge, mais vous avez l'autorisation de scripter des requêtes répétitives.
https://en-construction.404ctf.fr
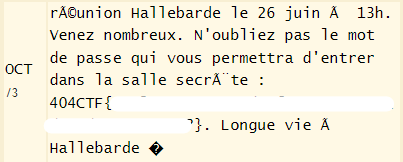
Solution: To solve this challenge, you need to find a way to get the flag. I looked for the flag by applying the basic methods of web attacks (code analysis, Directory Transversal...). But unfortunately that didn't work. So I couldn't find anything... That's only after the end of the CTF, that I found the solution thanks to bouloukaouze. To explain her method, he noticed that when he change page https://en-construction.404ctf.fr/page/ x, the status code value change. So he made a python script to get all status code :
import requests
url = "https://en-construction.404ctf.fr/page/%s"
retour = ""
for i in range(3,334):
r = requests.get(url % i)
retour += str(r.status_code)[1:]
print(retour)When the code is executed, we get these values : 16230325116515615115715604011014115415414514214116214414504015414504006206604015216515115604030324004006106315005604012614515614517204015615715514216214516517005604011604715716514215415114517204016014116304015414504015515716404014414504016014116316314504016116515104016615716516304016014516215514516416416214104014404714515616416214516204014414115616304015414104016314115415414504016314514316230325016414504007204006406006410312410617310416206015406313710406313715506013106311613714406313714606406116206313712006416312306316213714406312313714406015611606306316313715606011607717505604011415715614716514504016615114504030324004011014115415414514214116214414504004
These are ASCII code that can be decipher with this website :
Last updated