Du gâteau
Category: Web - Points: 993 - Difficulty : Moyen - Solves : 94
Description: Nous avons découvert que Hallebarde utilisait une pâtisserie comme couverture pour leurs activités criminelles. Visitez leur site web et voyez si vous pouvez accéder à leurs secrets. https://du-gateau.404ctf.fr
Solution:
To solve this challenge, we need to find how to bypass the cookie verification.
When we are going on the webpage we can see a "normal" website :
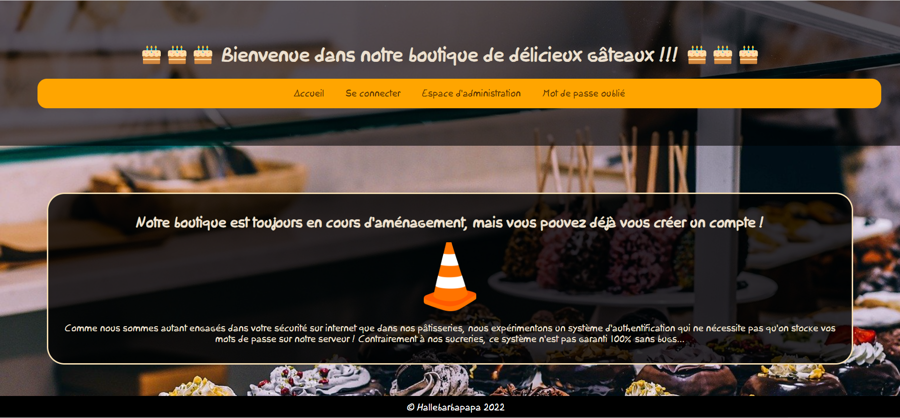
When we try to access to the "Espace d'administration" page, we get this error message :
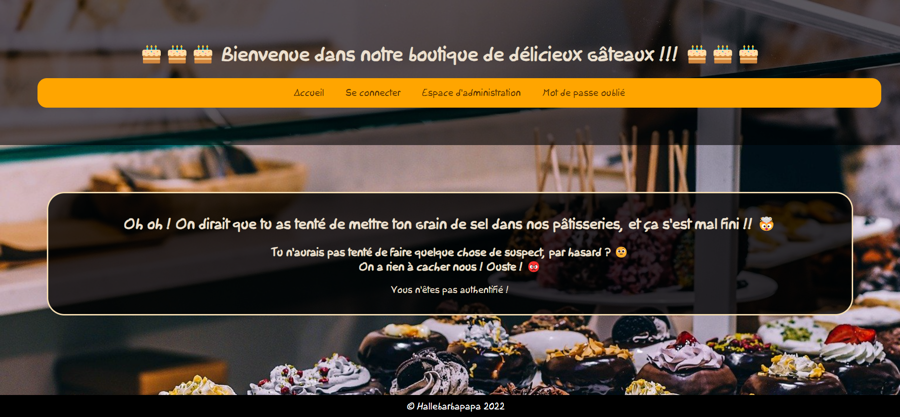
To understand how the user cookie is generate, we fill the inputs of this page (username : test / password : 1234) :
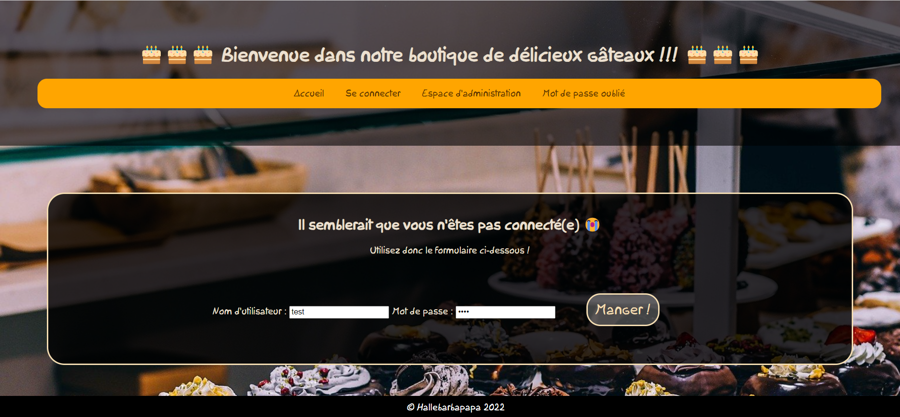
We get this cookie : auth=dXNlcm5hbWU9dGVzdDtwYXNzd29yZD1kNDA0NTU5ZjYwMmVhYjZmZDYwMmFjNzY4MGRhY2JmYWFkZDEzNjMwMzM1ZTk1MWYwOTdhZjM5MDBlOWRlMTc2YjZkYjI4NTEyZjJlMDAwYjlkMDRmYmE1MTMzZThiMWM2ZThkZjU5ZGIzYThhYjlkNjBiZTRiOTdjYzllODFkYg==; who is encoded on Base64.
When we decipher it, we get this : username=test;password=d404559f602eab6fd602ac7680dacbfaadd13630335e951f097af3900e9de176b6db28512f2e000b9d04fba5133e8b1c6e8df59db3a8ab9d60be4b97cc9e81db with the good user (test) and the password encrypted with sha-512.
Now we need to make the site believe that we are logging in as admin with this cookie format: username=Ayweth20;password=46a72ac861e946e09419cf10786d092e283c60fba5fa78ab7bd55d77d3d7a80ef3d98b7f155556f4e9f5b5593485295872fc6bdf695263f62133be16271ef69d;username=admin;password=. With this method the site will check the first username (test) and the password but in reality we will connect with the second username (admin). We convert this cookie in Base64 and send it to the website :

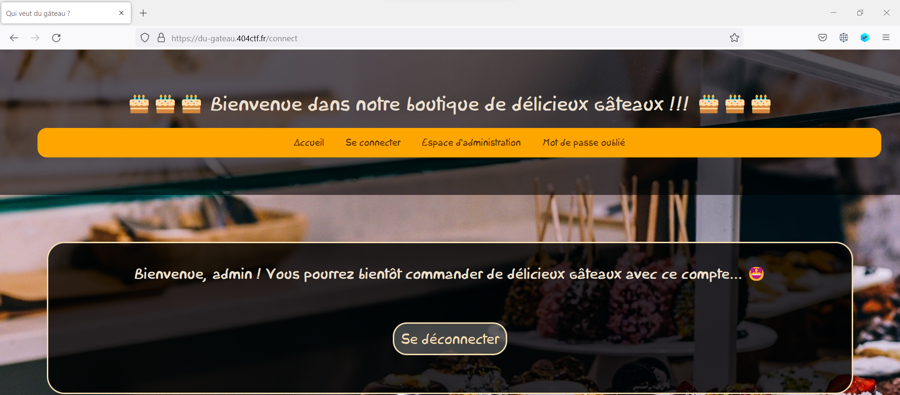
Now we are connected the admin account 🤩
We can access to the Mot de passe oublié webpage to try to find the account password. But after some tests, we are looking that the password are very difficult to find.
And when we click on the submit button we can't see any request in the traffic. So that means that the verification is doing on user side (and so maybe we will find the password hash).
Yes that's good. When we try to find the password, the webpage code contain this function (with the good hash) :
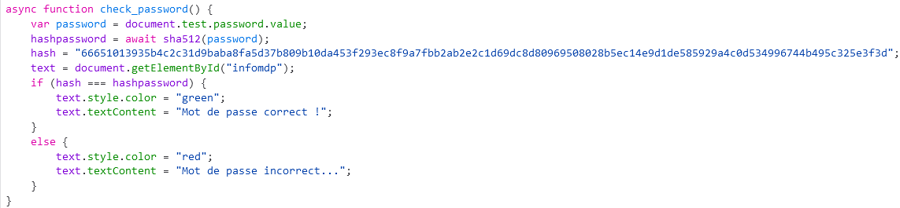
Now we have the username : admin and the password hash : 66651013935b4c2c31d9baba8fa5d37b809b10da453f293ec8f9a7fbb2ab2e2c1d69dc8d80969508028b5ec14e9d1de585929a4c0d534996744b495c325e3f3d
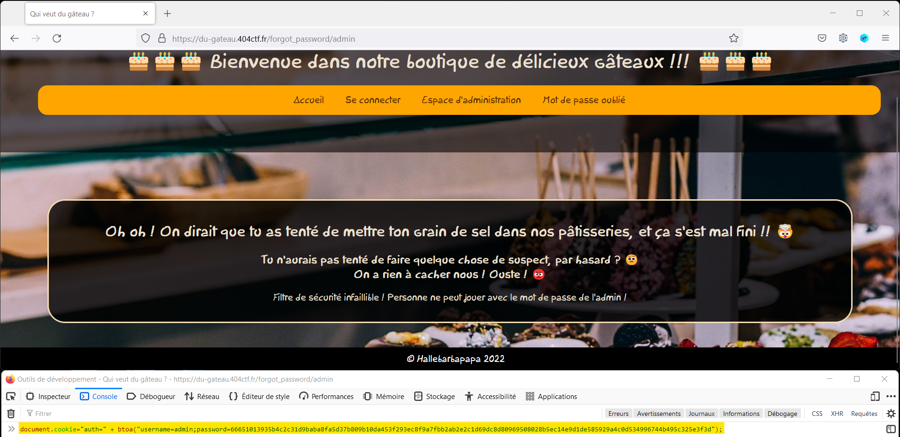
Damn ! This method not work... 😢
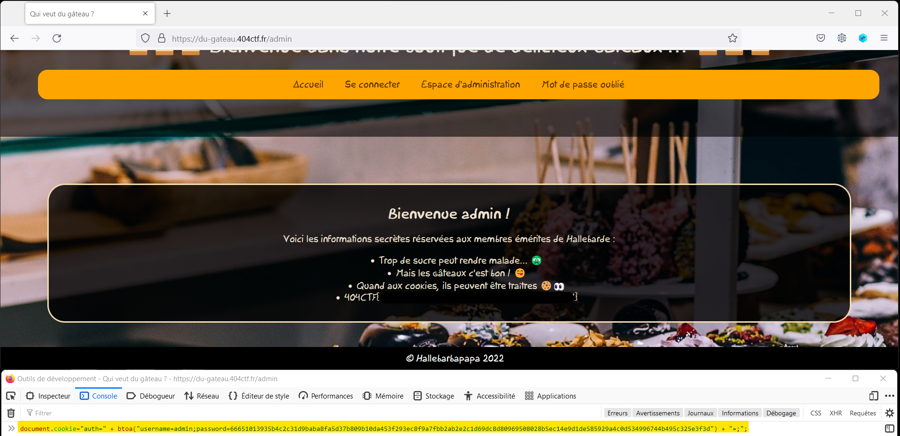
After the end of the CTF, I search an other writeup to understand how to finish the challenge. I saw on this writeup that I miss just one = at the end of the cookie.
The good cookie is : document.cookie="auth=" + btoa("username=admin;password=66651013935b4c2c31d9baba8fa5d37b809b10da453f293ec8f9a7fbb2ab2e2c1d69dc8d80969508028b5ec14e9d1de585929a4c0d534996744b495c325e3f3d") + "=;";.
Last updated